Advanced Private Networking
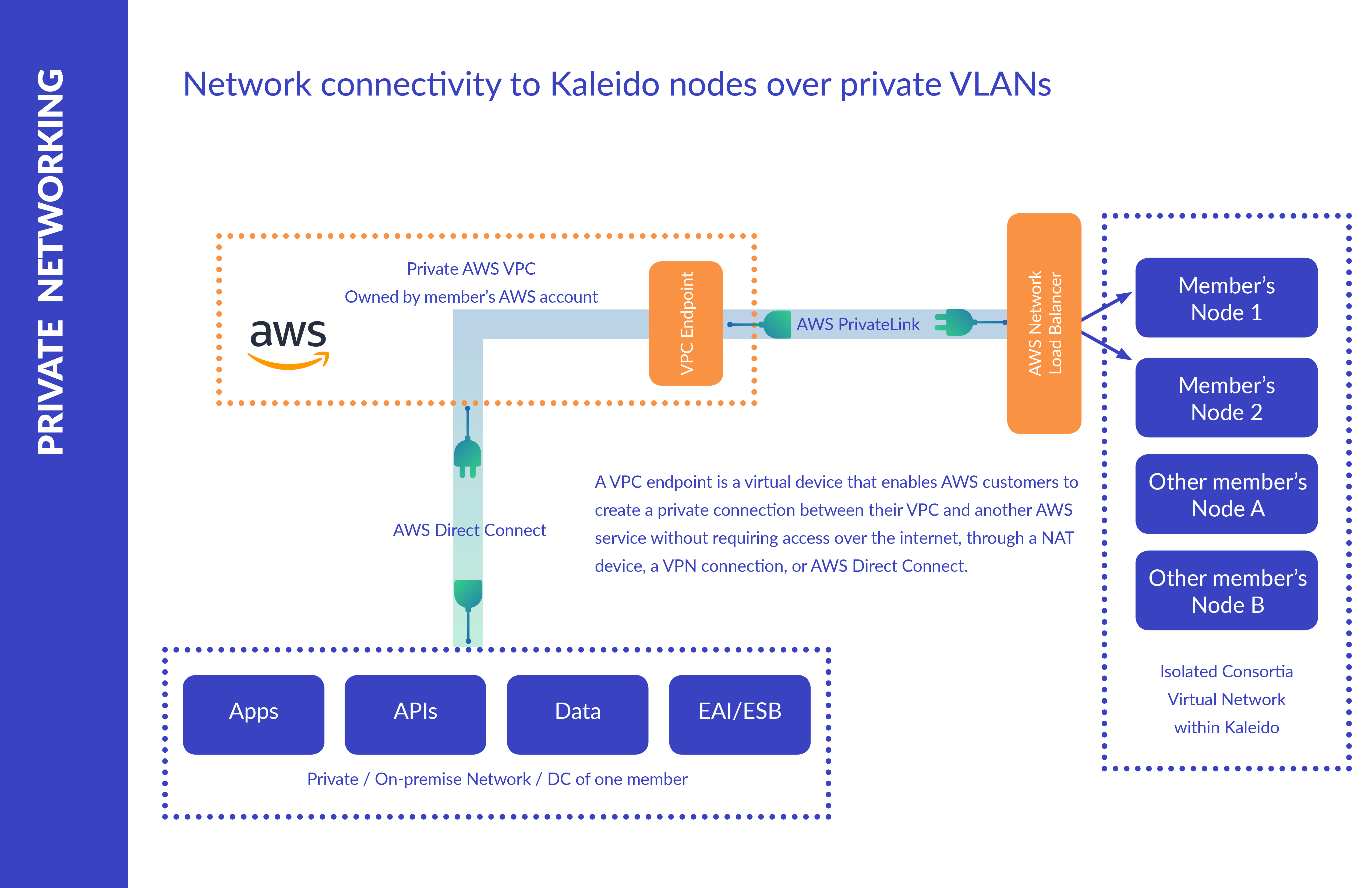
There are a variety of circumstances (e.g. sensitive data, security regulations, etc.) where it may be desirable or possibly mandated to communicate with the Kaleido network via non-public routes. To accommodate this requirement, Kaleido offers the ability to configure nodes with a private ingress and connect through your AWS Virtual Private Cloud (VPC) via a PrivateLink endpoint. This ensures that all traffic passing through the node’s private ingress will emanate from your virtual cloud network and remain completely isolated from the public internet.
The extent to which private networking is enforced is at the complete discretion of the organizational admin overseeing the configuration(s). Public and private ingresses are not mutually exclusive, meaning that the node can be configured to accept connections through either gateway if the public ingress remains enabled. This provides organizations with complete control over their networking layers and allows for private and public streams to be partitioned accordingly. The only stipulations for private connections are the presence of the Ethereum-compatible applications/resources in your VPC and a PrivateLink endpoint provisioned against the Kaleido service. Kaleido does not generate separate hostnames for nodes with a private ingress, thus allowing for developers to orchestrate the RPC or WebSocket provider calls in the same manner as they would for a standard public connection. VPC networking orchestrations (internet gateways, network address translation, etc.) do not interfere with the ability to connect privately to a Kaleido node and should be maintained by the relevant AWS admin user(s) in accordance with their organization’s standards .
Generating a PrivateLink Endpoint
- Access the Kaleido console and open the Feedback tool. Select Other as the purpose of the inquiry and in the body of the request supply your AWS Account ID and a short sentence requesting access to the Kaleido PrivateLink endpoint service. Kaleido requires your AWS Account ID in order to whitelist your AWS Organization and expose the service.
- Wait for a confirmation from the Kaleido support center. Once the private endpoint service has been enabled, you can proceed to create the endpoint.
- Log into the AWS console and navigate to the VPC Service
- Click Your VPCs in the navigation panel and verify that both
DNS resolutionandDNS hostnamesare enabled for the target VPC. If they are not, the settings can be changed using the Actions drop-down menu at the top of the page. - Click Endpoints in the VPC navigation panel
- Click the Create Endpoint button at the top of the screen
- In the Service Category section select
Your AWS Marketplace servicesas the option - Select the regional entry ending in
.kaleido. You should see an entry name similar tocom.amazonaws.vpce.us-east-2.kaleidowithin the table. Note that the AWS region may differ depending on the hosting location of your VPC - Remain on this screen and use the VPC dropdown menu to select the intended target VPC for this endpoint (this should be the one configured for DNS in the previous steps).
- Select which Availability Zones (AZs) and corresponding subnets to enable the endpoint for. It is recommended that you select all available for your target VPC.
- Verify that
Enable Private DNS Nameis selected for the endpoint - Lastly, select the appropriate Security Group or create a new one if needed
