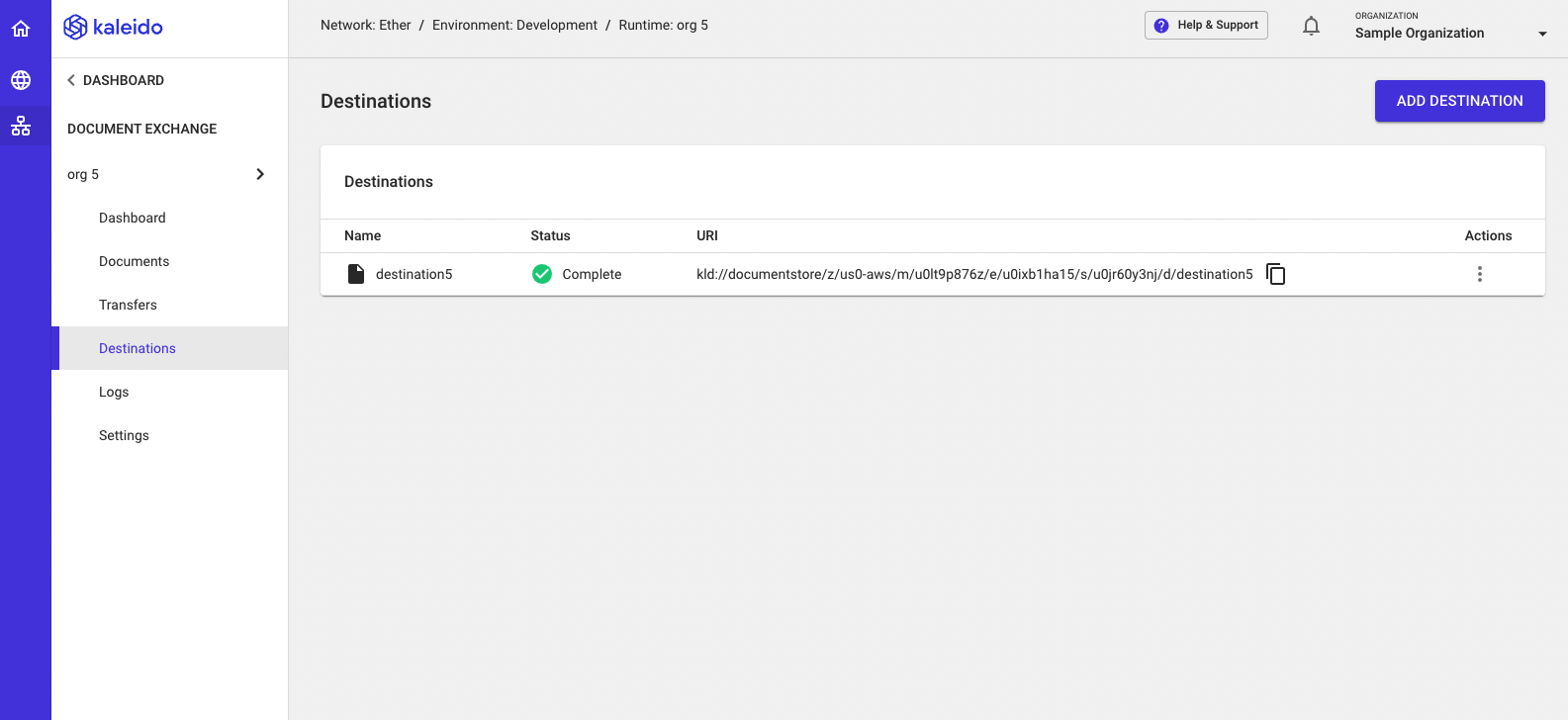
Document Exchange Destinations
A destination is a programmatically targetable URI for the secure submission of signed-and-encrypted messages. When you set up a destination in a Document Exchange runtime, you are giving others in your network an endpoint to target to share documents with you. Destinations are underpinned with their own unique digital certificate, which is used for the encryption of any messages targeting the destination. This ensures that only the possessor of the destination's private key is able to decrypt the payload. This also allows the message recipient to authoritatively verify the identity of the sender.
NOTE: The Document Store service is reliant on the On-Chain Registry service. The certificate associated with each destination is stored in the On-Chain Registry membership profile. This makes it possible to query the destinations of all members in an environment through a convenient address book, while also providing access to all certificates for the encryption of messages and verification of signatures.
Prerequisite for Destinations
In order for a destination to be configured, the accompanying membership needs to have it's identity confirmed in the Network and Registered on On-Chain. If you are unsure of whether your membership meets these criteria, you can check the status by navigating to the membership in question within the Address Book where you should see two green checks next to Identity and Registered On-Chain with an accompanying certificate. See below for an example of both a sufficiently identitifed Membership on the left and an insufficiently identified Membership on the right:
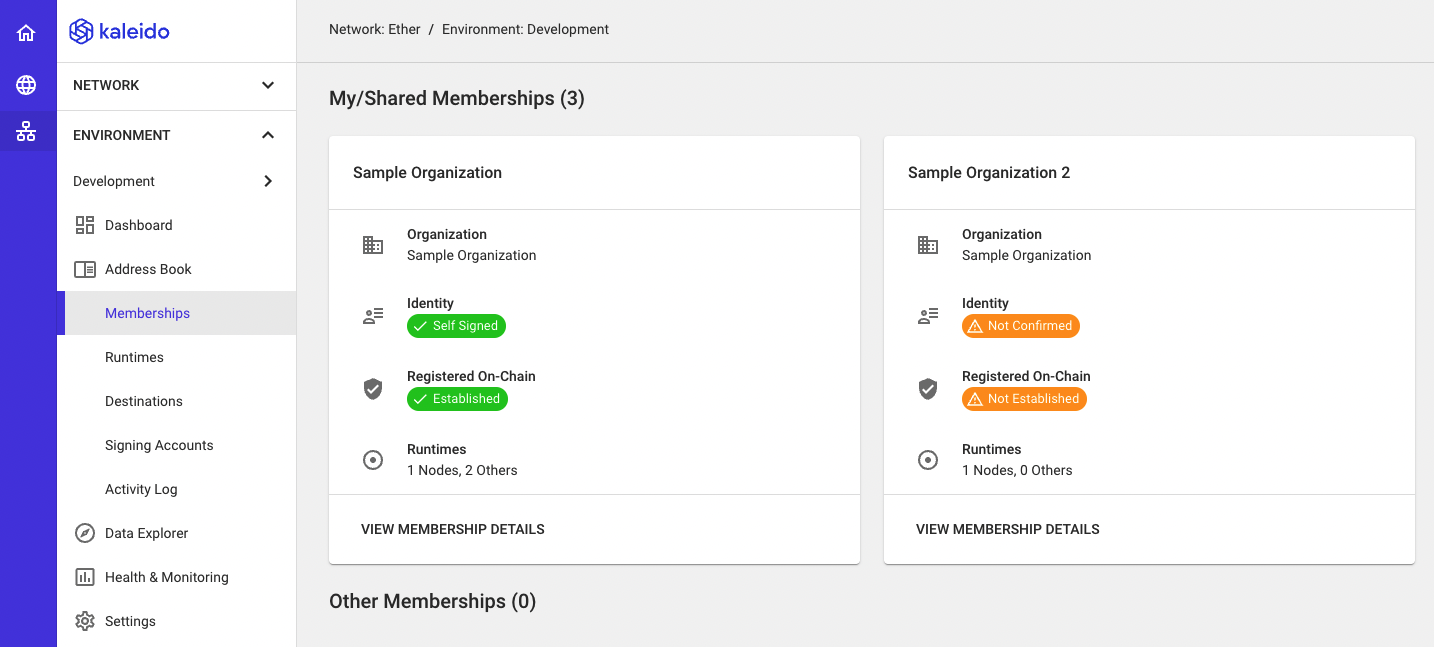
If your Membership has yet to be confirmed, follow these steps from here:
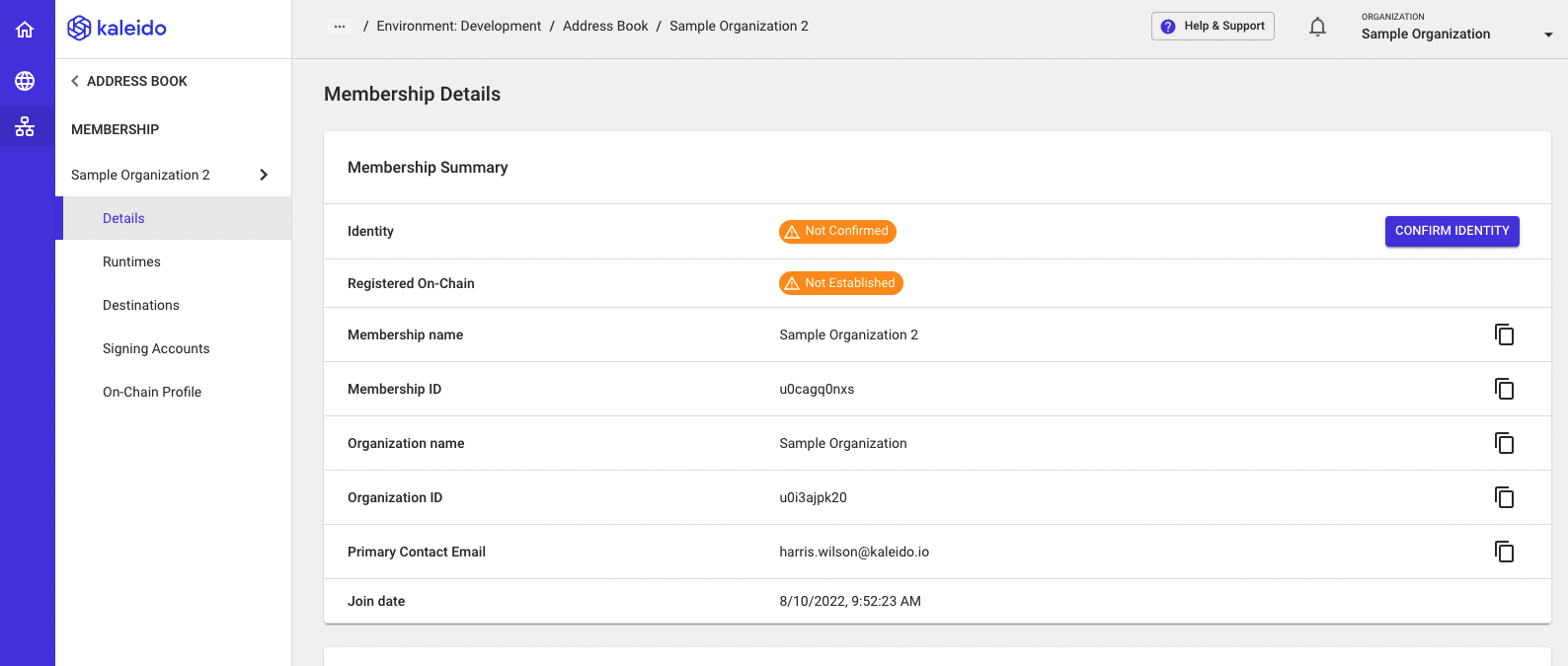
- Click View Membership Details and select Confirm Identity in the top right
You will now choose between generating a Self-Signed Identity Certificate or an Externally-Signed Identity Certificate. The recommended approach is to allow Kaleido to register your membership identity on chain with a self-signed identity certificate. This will allow you to create the destination immediately through the Kaleido console.
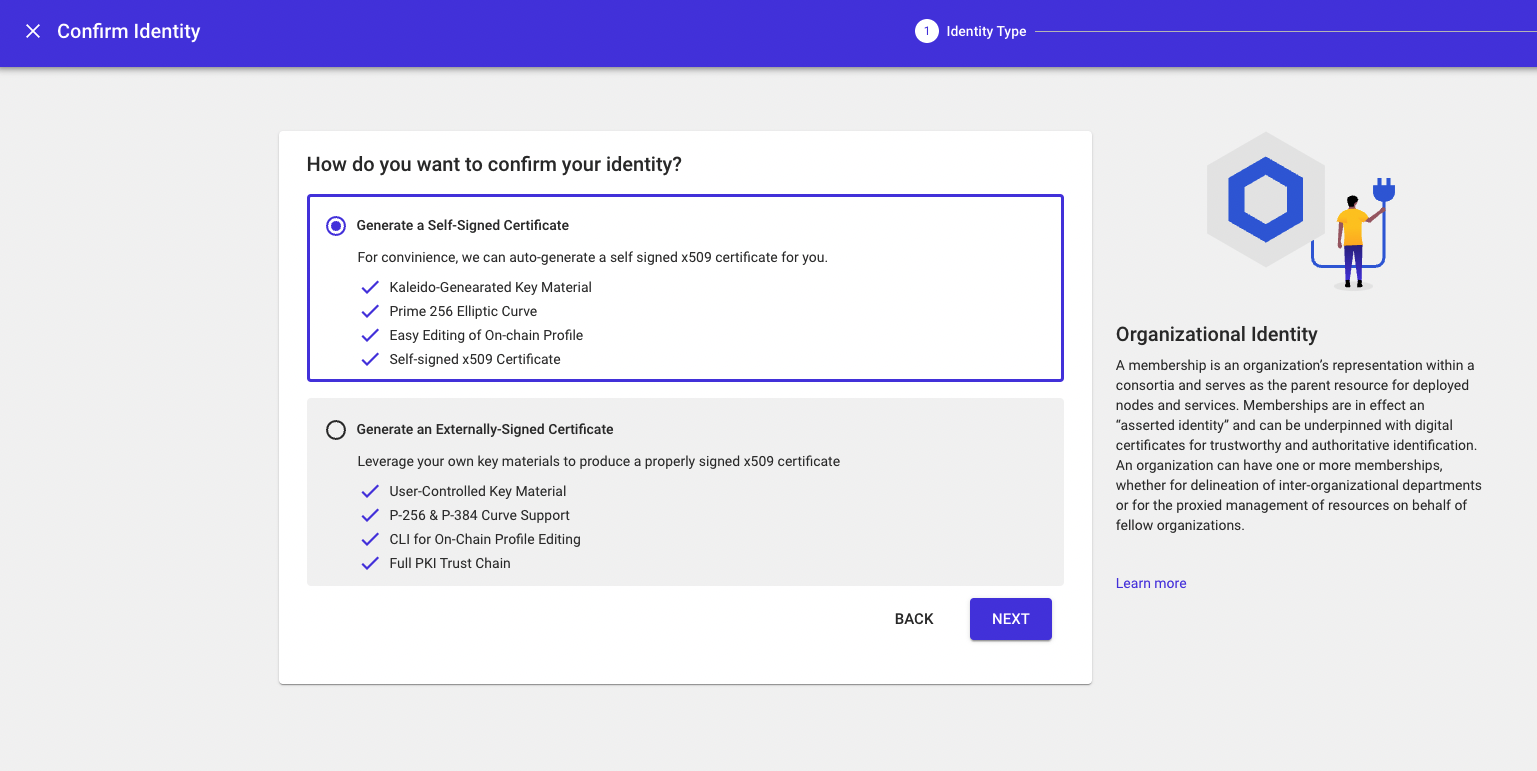
If you prefer to use an externally-signed certificate for your organizational identity, you will be responsible for using the Kaleido SDK to upload the destination certificate in order to prove ownership of the Ethereum account associated with your profile. To do this, you can follow the instructions to confirm your identity and generate a Kaleido-compliant x509 certificate. No matter the approach, Kaleido will handle generation of the destination certificate.
Destination Set Up for Kaleido Self-Signed Identities
- Click through to your Document Exchange runtime
- Click Add Destination
- If you followed the previous steps in the Prerequisite for Destinations section, your identity has already been established on-chain so you will only be prompted to create a Destination Name.
- If your identity has not been established on-chain, you will be given the option to let Kaleido generate a certificate for you and register it on-chain, then you will be prompted to create a Destination Name.
- Click Finish and your destination should show up with a Complete status and now be available as an endpoint for other users in your environment.