Tenancy & Isolation
Kaleido has robust processes implemented to ensure the proper protection of critical key materials, secure virtual networking, strong authentication schemes, highly available runtime components, firewalls and logical isolation, encrypted transport, cross-cloud tunneling and disaster recovery. The content in this section will explore these security and cloud architectural components, with an aim to address the core concerns of IT Ops professionals and organizational risk officers.
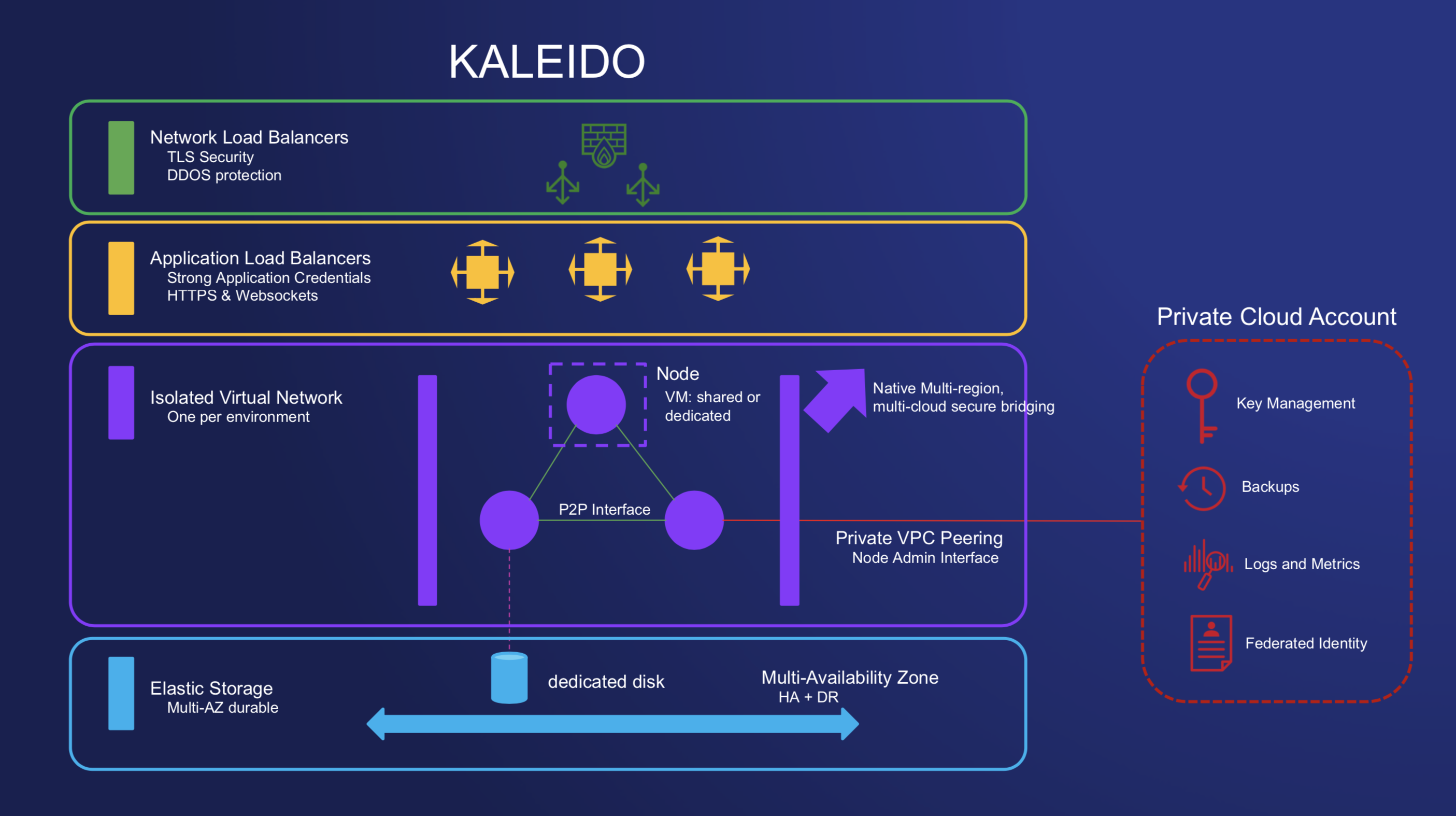
Network Layer
- Cloud native load balancers - ELB (elastic load balancers) and NLB (network load balancers)
- Serves a CA-signed and validated certificate for identity and validation
- TLS secured allowing for connection over HTTPS
- Default DDoS protection via the cloud native infrastructure services
Application Layer
- Connections are ultimately targeting the node ingress
- Nginx utilized for HTTPS calls
- HA Proxy utilized for WebSocket calls
- Application Credentials (strongly generated username password) combinations authenticate access to the ingress.
- Kaleido does not persist plaintext username secrets, rather a salted hash is kept and used for verification
- Verified calls are granted access to the isolated virtual network encapsulating the blockchain layer
Environments and Nodes
- Logical isolation per Kaleido network (environment)
- Network policies are used to isolate multi-tenant virtual environments across a shared VM pool
- Support for fully-dedicated VMs is available upon request to Kaleido
- Nodes are able to peer and gossip securely within their isolated environment
- Firewalls ensure no data leakage across isolated environments
- Resources are confined solely to the environment in which they are created. For example, application credentials in Environment A are unusable in Environment B
- Option for secure integration with user-controlled native cloud services. File system and key encryption, log streaming, file system backups and private connections.
- REST API Gateway available for idempotent at-least once delivery transaction submission via Kafka
- Event streams on a per-method subscription within smart contracts can send customized event payloads via Kafka to enumerated URLs
Storage
- Elastic File System instances are mounted on nodes to support on-demand scaling
- The cloud native file systems come with default High Availability and Disaster Recovery safeguards built in
- Dedicated directories of the elastic file systems are mounted and provisioned to each node ensuring data isolation in a shared virtual environment
- KMS integrations can be used to further encrypt anything written or mounted in the filesystem
