Organizations and Users
Every user of Kaleido gets their own Kaleido Organization and can add other users/administrators to that organization.
You named your Kaleido Organization when you signed up for Kaleido, but you can change it. If you don't remember applying an arbitrary name, your org will default to "My Company Organization."
As your organization's owner, you are the sole administrator who can add/remove users, manage billing details, or upgrade to a different plan level.
You also have the ability to create "sub-orgs" beneath your parental/root organization. Sub-orgs are unilaterally owned and controlled by the parent organization and offer a unified administrative domain over multiple separate sets of resources. By default, the billing for the sub-org will initially be rolled up into the root organization. If necessary, the ownership CAN be transferred after the fact, and the sub-org can be detached from its association for separate management and billing administration. See below for more information on organization management and sub-orgs.
Managing your organization
- Click the user icon in the lower lefthand corner of the console
- Select "Manage Orgs"
- Beneath your org name, click "Manage Organization"
- This will take you to the management dashboard
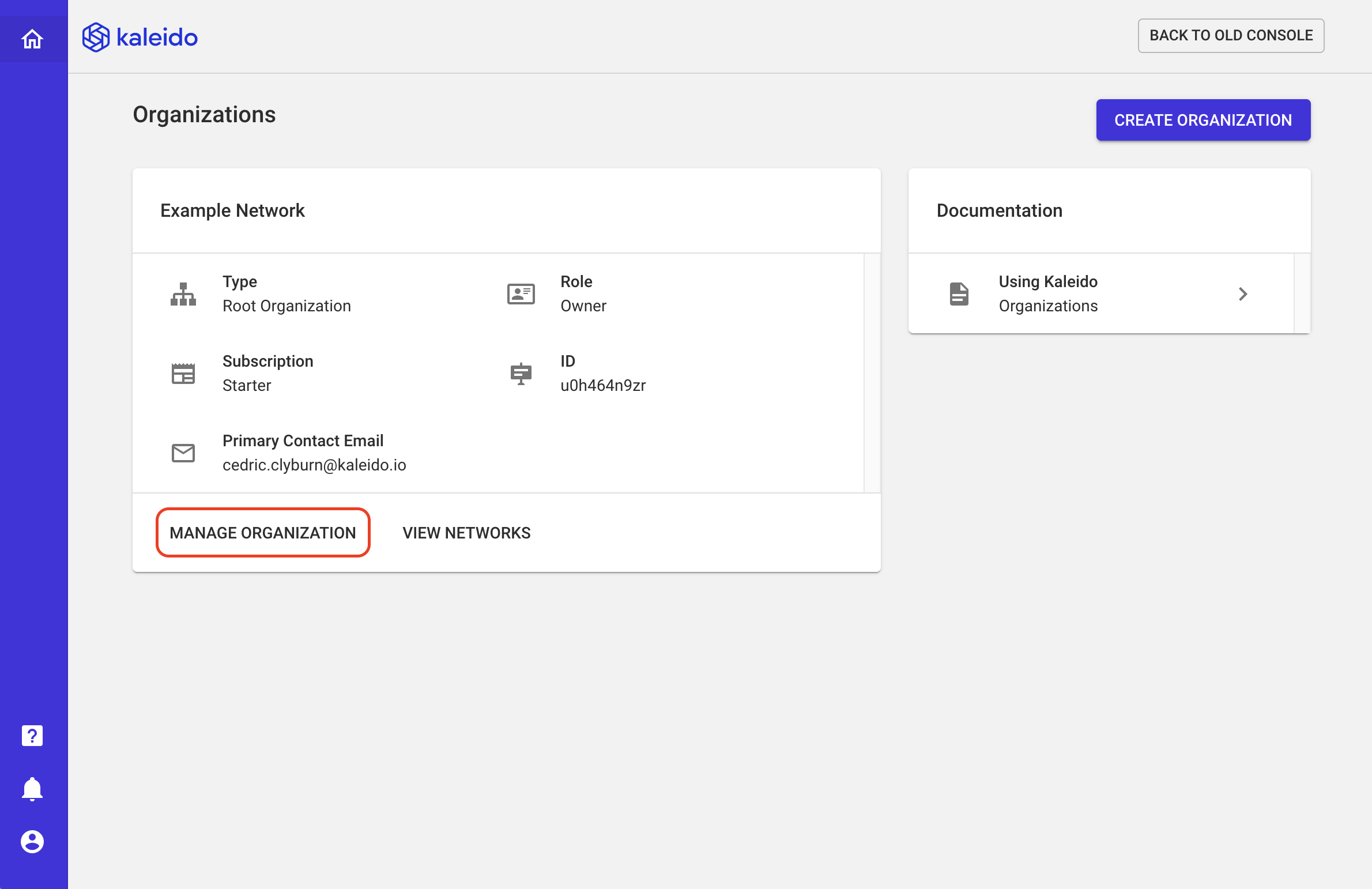
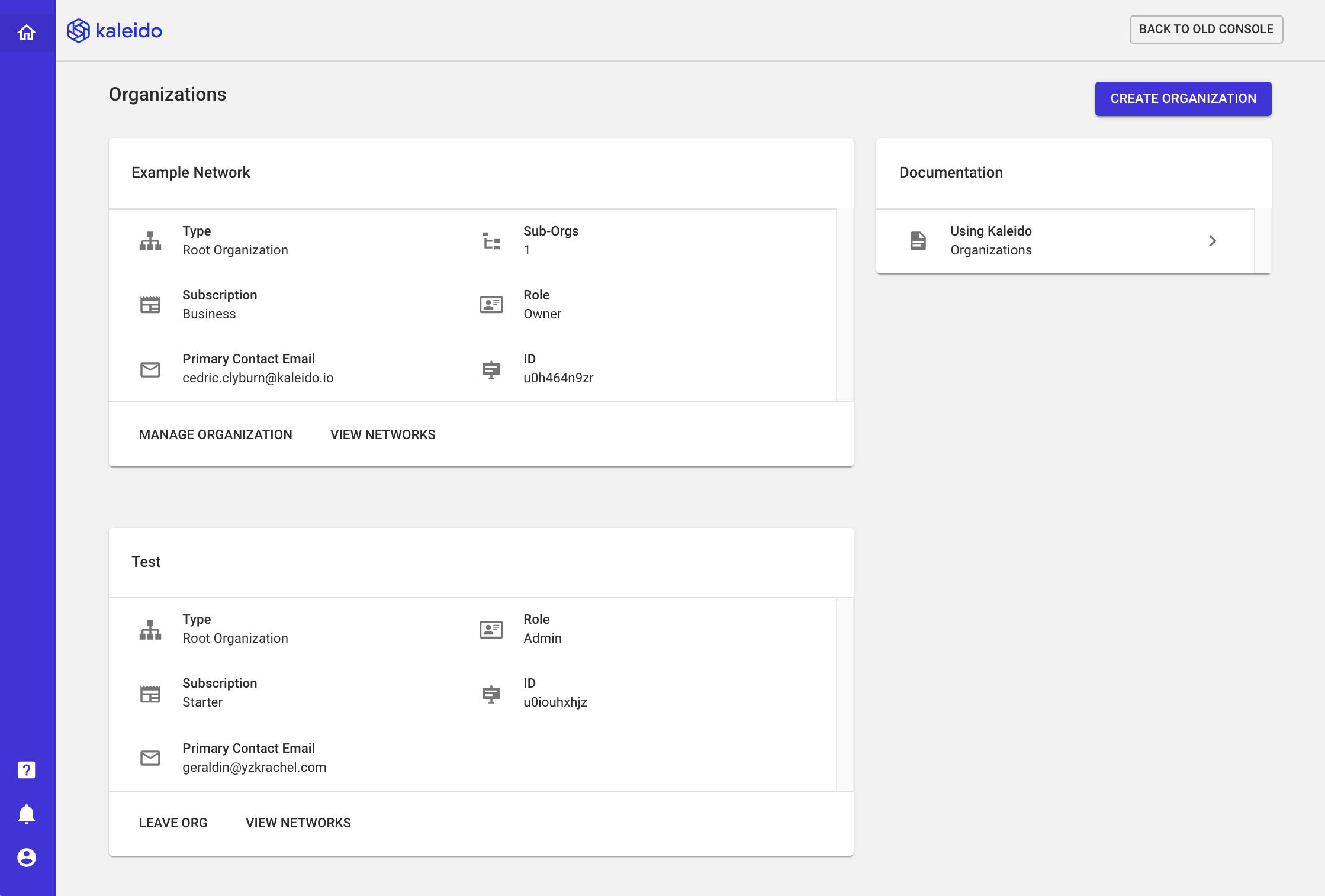
If you have been invited to other organizations, you will see them listed here too. In the below screenshot, the user is the Example Network org owner and has been invited as a co-administrator to the Test org.
Adding users to your organization
You can add additional users to your organization, so that when they log in with their own email, they will be able to access the Kaleido resources (consortia, environments, nodes, and services) owned by your organization. This is a useful approach for scenarios where an organization benefits from a shared workspace for collaboration and iteration.
- Click the "Manage Users" tab in the lefthand navigation
- Click the "ADD USER" button in the upper righthand portion of the screen
- Use the email address bound with the user's Kaleido account.
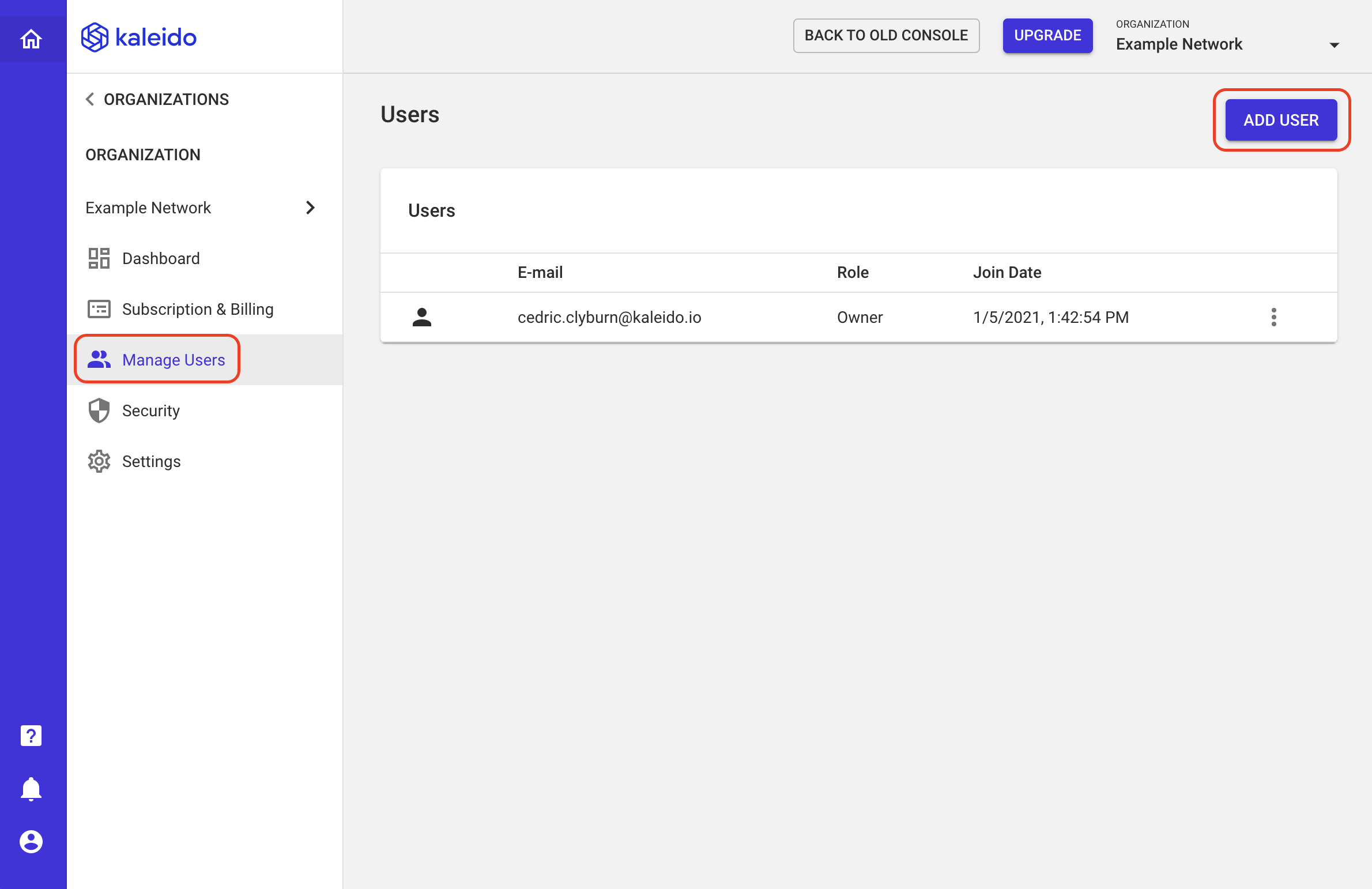
- You can remove users at any time from your organization. Simply click the dropdown ellipsis next to their email address and select "Delete User"
- Only the organization owner can invite and remove users.
- Only the organization owner can initiate subscription upgrades/downgrades.
Sub Orgs
- Click "Dashboard" in the lefthand navigation to access your organization management portal
- Click "Create Sub Org" within the "Relationships" modal
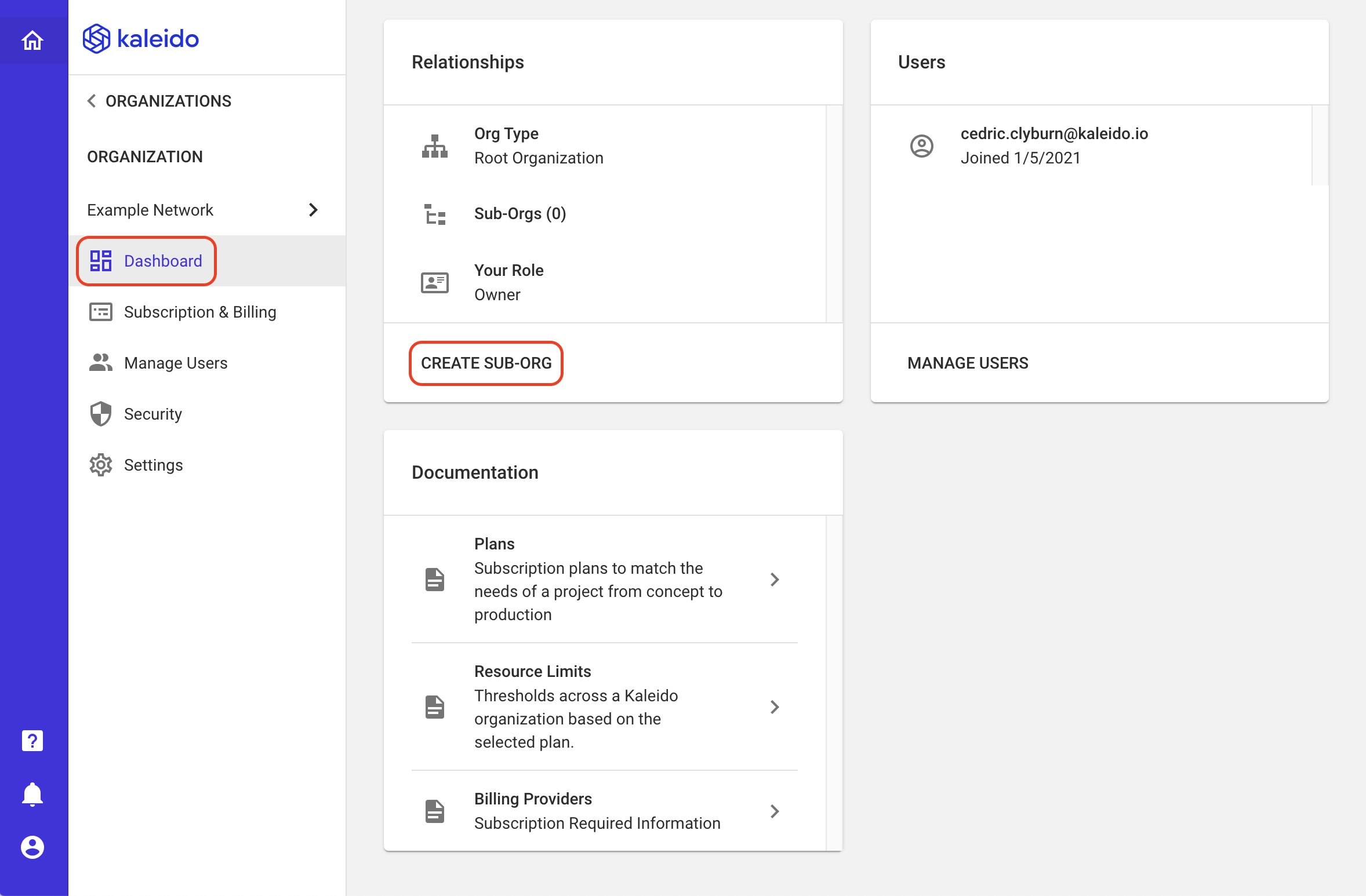
- Input a name for the new organization
- If you are the owner of multiple root organizations, use the dropdown to select the desired org. (Ownership of organizations can be transferred in certain circumstances, and sub-orgs can also be detached after the fact. As a result, there is potential to be the owner of multiple root organizations.)
- Optionally use the Advanced Settings dropdown to modify the sub-org's Home region and/or the contact email associated with it.
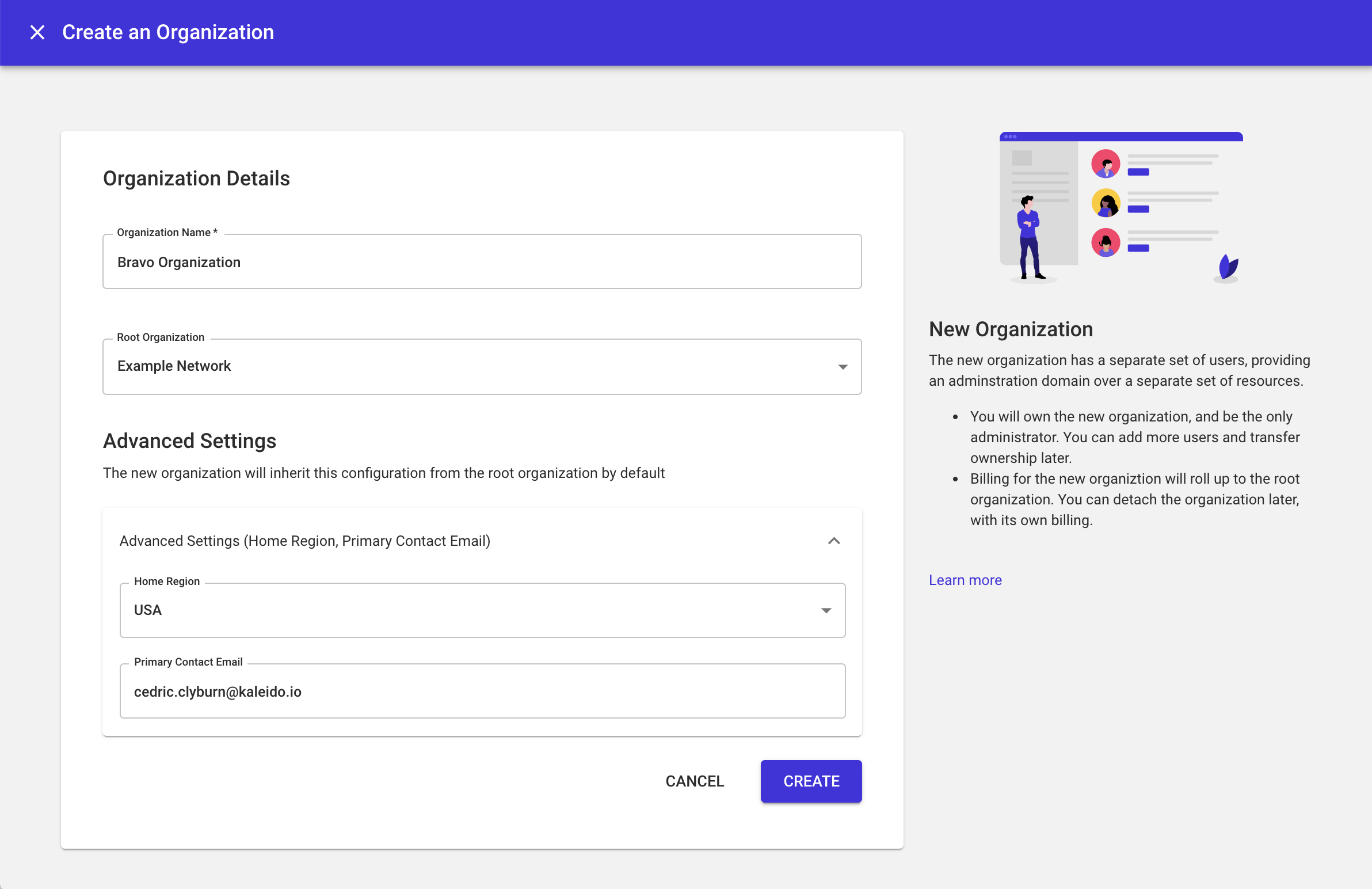
- Click CREATE to provision the new sub-org
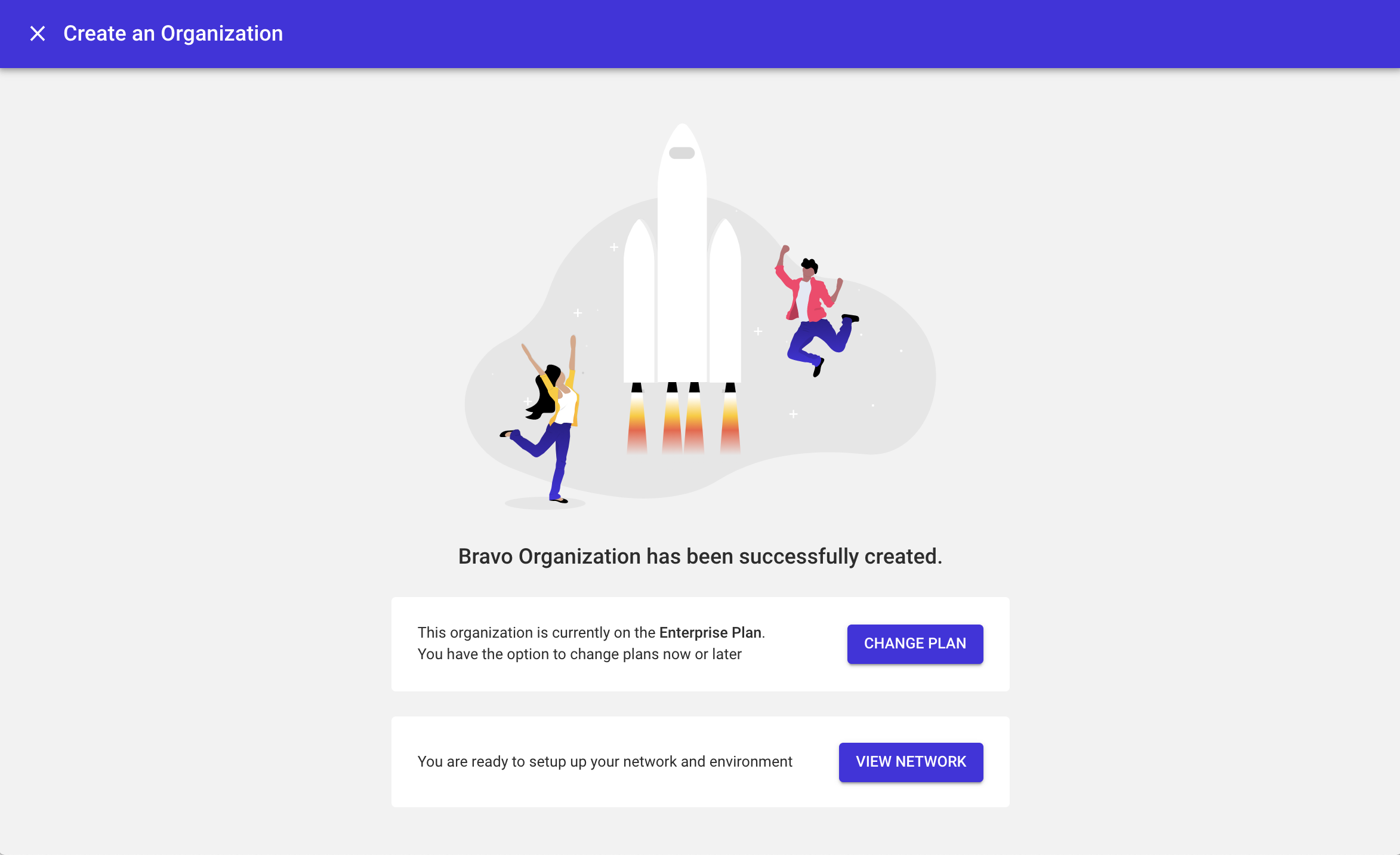
- Upon success, you will see a notification screen with the option to change the current plan or deploy resources
Managing a Sub Org
- Use the org switcher dropdown in the upper right-hand portion of the screen to switch to a sub-org
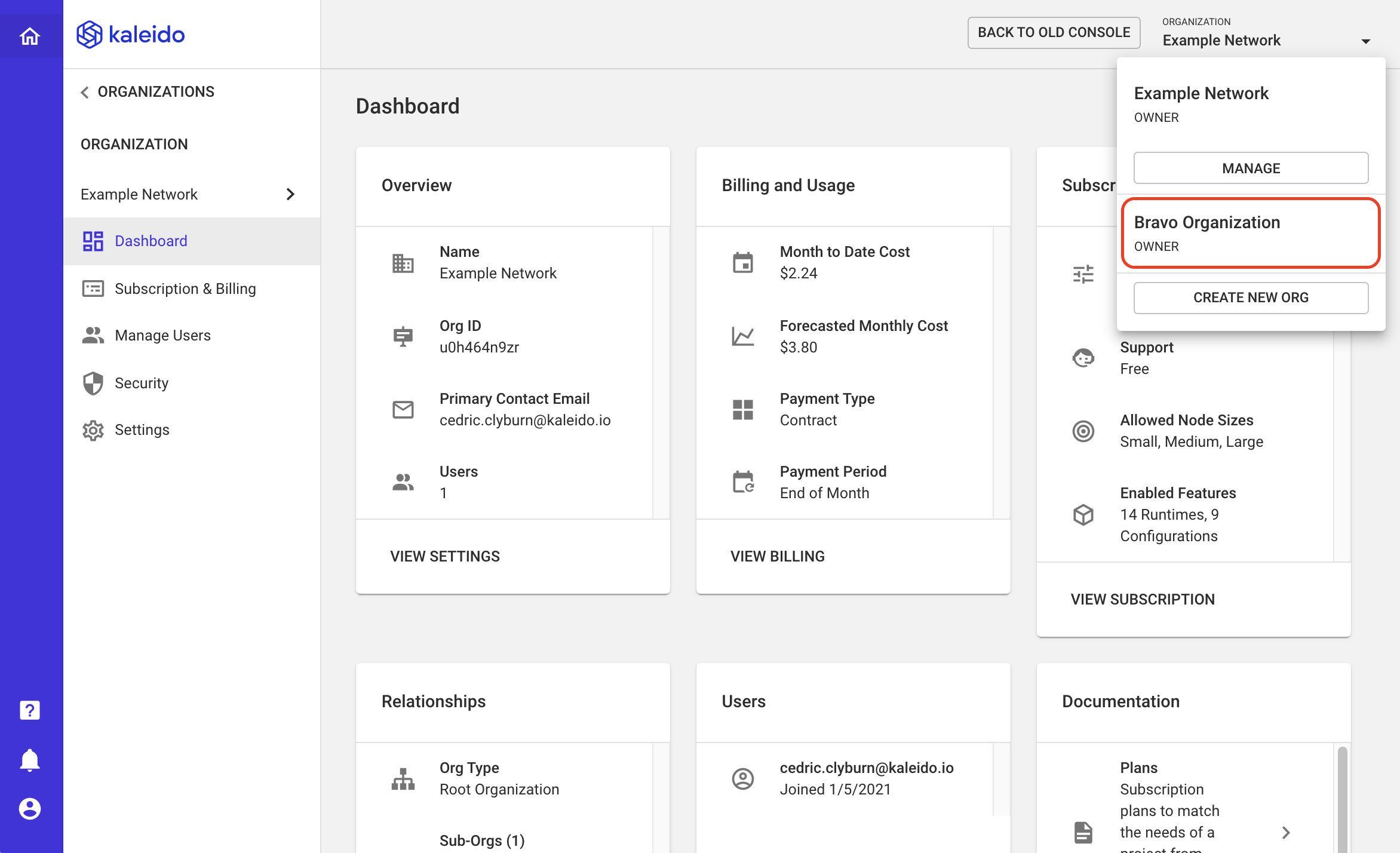
- You can also use the lefthand navigation within your organizational management portal
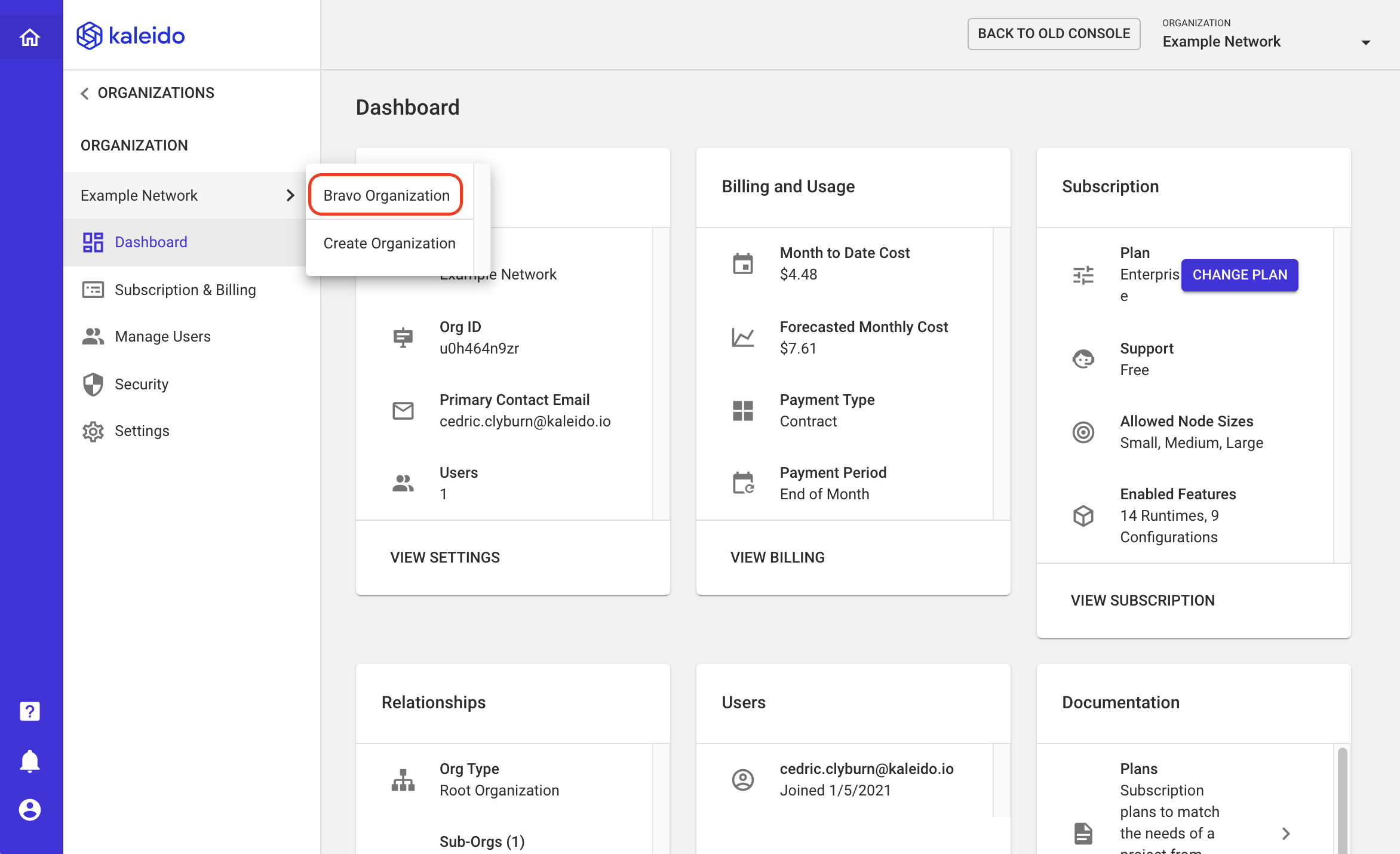
- Subscription and Billing - use this to alter plans or see current and forecasted billing
- Manage Users - use this to add or remove users
- Security - optionally enforce or remove multi-factor authentication on the sub-org
- Settings - use this to change the name, transfer ownership or alter the associated email
Once you are operating under the context of the sub-org, you can proceed to deploy and manage resources in the same fashion as you would for your root organization(s).
