Blockchain Application Firewall Introduction
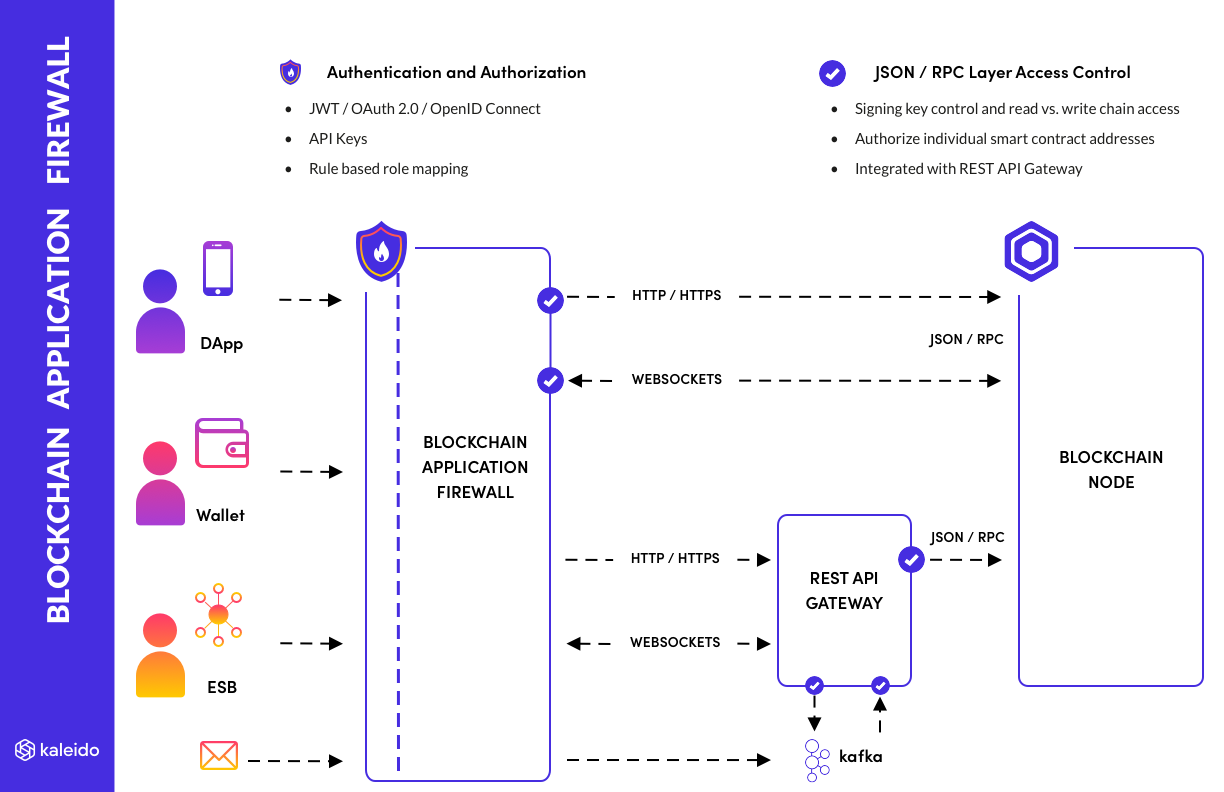
The Kaleido Blockchain Application Firewall (BAF) provides rich options for authentication and authorization of application connections to your Blockchain resources.
Similar to how a Web Application Firewall (WAF) would operate for your web-based application tier, it sits between your blockchain applications and your node to provide a reverse proxy and gateway security tier.
Example use cases
The blockchain application firewall has a range of uses.
OAuth 2.0 / OpenID Connect Security with an Identity and Access Management (IAM) server
The blockchain application firewall can be configured to trust your IAM server, such as a private instance of KeyCloak, Otka, Microsoft Azure Active Directory, or any other system that issues tokens as signed JSON Web Tokens (JWT).
This allows standard OAuth based sign-in for your blockchain applications, with an experience your users are familiar with from non-blockchain enterprise applications. Such as username+password login and multi-factor authentication (MFA), as part of an OAuth Authorization Code flow.
As a result of the OAuth flow the IAM server issues an access token in the form of a JWT containing details about the user. For example whether they are authorized to sign transactions on the blockchain, or which signing keys they are allowed to access. This user to role mapping is maintained in your IAM system, and the blockchain application firewall can apply it as a policy to the REST and JSON/RPC calls that user is allowed to make against the blockchain.
Restricting/mapping access to signing keys
It is popular to allow Kaleido to manage signing of your blockchain transactions. Maybe using on-platform wallets (protected by KMS), or via our hierarchically deterministic (HD) wallets, or even using off-platform Cloud HSM capabilities where the keys never leave your own cloud account.
This signing is integrated with our REST API Gateway that handles ordering of the transactions, and horizontal application scale - as well as simplifying your applications by providing REST APIs similar to any modern web-based system.
In these scenarios you might have many signing keys being managed by Kaleido. Maybe keys for different teams within an organization, or keys for different types of operation, or maybe thousands of keys allocated to individual users of your application. You need to restrict access to signing with these keys, only to authorized connections.
The blockchain application firewall analyzes each JSON/RPC request as it passes through, checking for attempts to sign transactions and authorizing them against a rule-set that specifies which keys are allowed to be used by that connection.
This capability works in tandem with your application level security. You can configure static rules to configure access to keys, or dynamic rules based on issuing JWT tokens in your application tier or IAM system to restrict signing access.
Connecting web/mobile wallets to your node with limited access
In some applications the identity/key that signs the transactions is owned directly by the end user (rather than being first mapped to an organizational identity/key to sign the transaction).
In these cases the signing key usually exists in a wallet on the client device or browser.
- A hardware backed wallet on the customer's smart phone
- MetaMask running in the user's web browser
This requires the application to be able to submit pre-signed transactions to the blockchain node. So the JSON/RPC interface of the node needs to be exposed to the application for sending the transactions.
The blockchain application firewall provides an additional layer of security for these connections, on top of the default boundary security built into the Kaleido platform.
- Restrict the operations that can be performed over the connection to the node
- Restrict to externally signed transactions only
- Restrict the contract addresses an application can submit transactions to
- Provide read-only access to the node, over REST API and JSON/RPC
- Limit access to historical block information, beyond receipt checking by hash
CORS configuration
The blockchain application firewall also allows the Cross-Origin Resource Sharing (CORS) configuration for the node to be adjusted and restricted, to match the requirements of your web-based application tier.
