Hyperledger Fabric CA Introduction
Hyperledger Fabric relies on certificates for identity and permissioning purposes. To assist in the set up and administration of Fabric networks, a Fabric Certificate Authority (CA) server is provided. For more details of the functionality of the Fabric CA server, refer to the official documentation.
Kaleido makes the Fabric CA server available for every membership in a Fabric environment. It can either be provisioned via the platform API, or it will be automatically provisioned when the first orderer node of the membership is added to the environment.
Self-signed root CA
By default, a Fabric CA server in Kaleido uses a self-signed root certificate based on a unique signing key, which is generated when the CA service is provisioned. A self-signed root certificate looks like the following:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
03:c1:f9:e7:d6:97:f0:27:88:52:09:47:44:93:44:c6:d7:9d:2a:56
Signature Algorithm: ecdsa-with-SHA256
Issuer: CN = fabric-ca-server
Validity
Not Before: Jan 4 15:04:00 2022 GMT
Not After : Dec 31 15:04:00 2036 GMT
Subject: CN = fabric-ca-server
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:5a:48:c7:8d:65:16:bf:1f:e9:fa:9b:47:d3:7f:
10:8a:78:ab:c0:94:50:4e:00:a0:19:9e:50:88:45:
2f:7d:6d:8f:b8:2b:16:d7:6a:77:68:65:24:ce:0a:
b2:1c:cd:67:0c:b3:3b:a2:4b:09:a9:60:fa:21:82:
78:06:b9:0c:23
ASN1 OID: prime256v1
NIST CURVE: P-256
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Subject Key Identifier:
D9:92:56:22:F0:D5:13:C1:C6:A7:76:F6:0B:79:89:5A:78:5B:A9:EE
Signature Algorithm: ecdsa-with-SHA256
30:45:02:21:00:d0:0c:00:10:3a:db:eb:57:62:0a:81:4c:49:
cc:09:db:4a:85:45:3b:96:16:00:0b:48:d1:18:d6:55:09:c3:
0b:02:20:31:47:ad:17:ae:b6:67:6a:e2:b3:76:96:5c:36:78:
0d:0e:2a:e9:5c:d2:66:97:80:4d:e4:2b:8d:7b:f2:5e:eb
Intermediate CAs
Sometimes the Fabric CA to be provisioned must be part of an existing PKI certificate chain, under an existing Certificate Authority.
This effectively makes the Kaleido Fabric CA an intermediate CA.
An intermediate CA can be provisioned using one of the following two approaches, either using a pre-generated signing key and the corresponding certificate, or having the new CA server enroll with an external CA server upon initial startup.
Using pre-existing signing key and certificate
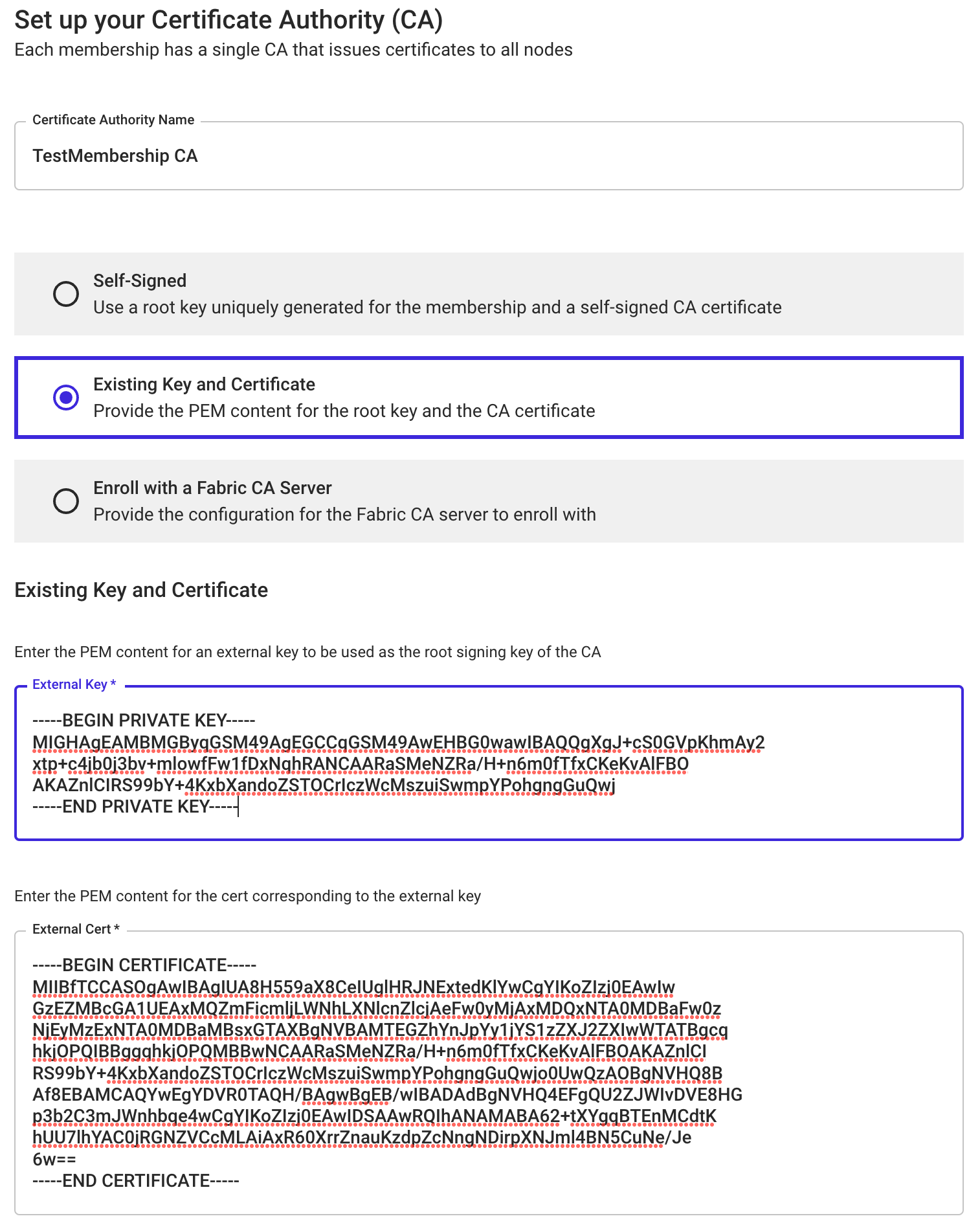
To configure the new CA server to use a pre-existing signing key and certificate, you must have the PEM encoded content of the private key (un-encrypted PKCS8) and the x.509 certificate.
If using the Kaleido console, select Existing Key and Certificate, then fill in the PEM content for the key and the certificate.
If using the platform API, see the example request below for reference:
curl -H "Content-Type: application/json" -H "Authorization: Bearer $APIKEY" -d '{"service":"fabric-ca","name":"ca-3","membership_id":"u0lehpq22z","details":{"external_key":"-----BEGIN PRIVATE KEY-----\nMIGHAgEAMBMGByqGSM49AgEGCCqGSM49AwEHBG0wawIBAQQgXgJ+cS0GVpKhmAy2\nxtp+c4jb0j3bv+mlowfFw1fDxNqhRANCAARaSMeNZRa/H+n6m0fTfxCKeKvAlFBO\nAKAZnlCIRS99bY+4KxbXandoZSTOCrIczWcMszuiSwmpYPohgngGuQwj\n-----END PRIVATE KEY-----","external_cert":"-----BEGIN CERTIFICATE-----\nMIIBfTCCASOgAwIBAgIUA8H559aX8CeIUglHRJNExtedKlYwCgYIKoZIzj0EAwIw\nGzEZMBcGA1UEAxMQZmFicmljLWNhLXNlcnZlcjAeFw0yMjAxMDQxNTA0MDBaFw0z\nNjEyMzExNTA0MDBaMBsxGTAXBgNVBAMTEGZhYnJpYy1jYS1zZXJ2ZXIwWTATBgcq\nhkjOPQIBBggqhkjOPQMBBwNCAARaSMeNZRa/H+n6m0fTfxCKeKvAlFBOAKAZnlCI\nRS99bY+4KxbXandoZSTOCrIczWcMszuiSwmpYPohgngGuQwjo0UwQzAOBgNVHQ8B\nAf8EBAMCAQYwEgYDVR0TAQH/BAgwBgEB/wIBADAdBgNVHQ4EFgQU2ZJWIvDVE8HG\np3b2C3mJWnhbqe4wCgYIKoZIzj0EAwIDSAAwRQIhANAMABA62+tXYgqBTEnMCdtK\nhUU7lhYAC0jRGNZVCcMLAiAxR60XrrZnauKzdpZcNngNDirpXNJml4BN5CuNe/Je\n6w==\n-----END CERTIFICATE-----"}}' https://console.kaleido.io/api/v1/c/u0a1k72cql/e/u0wrhhqt5w/s |jq
Using an external Fabric CA server
The new Fabric CA service can also be configured to dynamically enroll with an external Fabric CA server upon the initial startup.
In order to use this configuration, the CA's identity must first be registered with the external Fabric CA server. Reference the Fabric CA documentation for how to accomplish that. Note that the identity must have an attribute “hf.IntermediateCA” with a value of “true”.
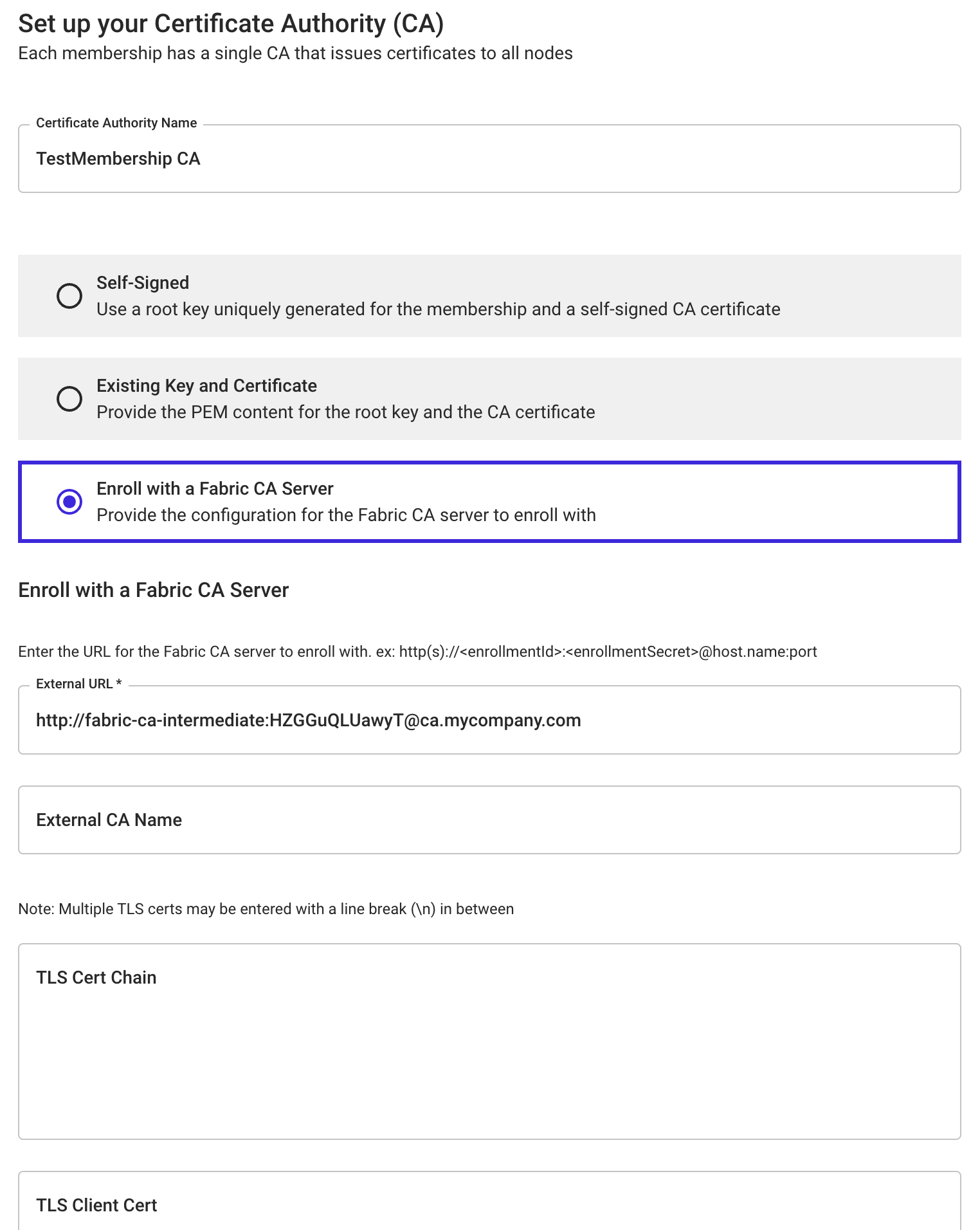
The URL for the external server must be in the following format: https://<enrollmentID>:<secret>@<parentserver>
If using the Kaleido console, select Enroll with a Fabric CA Server, then fill in the required parent server URL and TLS CA certificates if necessary.
If using the platform API, see the example request below for reference:
curl -H "Content-Type: application/json" -H "Authorization: Bearer $APIKEY" -d '{"service":"fabric-ca","name":"ca-3","membership_id":"u0lehpq22z","details":{"enroll_with_ca":{"parentserver":{"url":"http://my-intermediate-ca:yMpfXXXXXOmb@ca.mycompany.com"}}}}' https://console.kaleido.io/api/v1/c/u0a1k72cql/e/u0wrhhqt5w/s |jq
If the parent server endpoint requires TLS, you can specify the server TLS CA certificate chain in the following properties in the payload:
"enroll_with_ca": {
"parentserver": {
"url":"https://my-intermediate-ca:yMpfWnNFLOmb@d67f-208-1-60-238.ngrok.io"
},
"tls": {
"certfiles": [
"-----BEGIN CERTIFICATE-----\nfirst cert in the CA chain\n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----\n2nd cert in the CA chain\n-----END CERTIFICATE-----\n"
],
"client": {
"certfile": "-----BEGIN CERTIFICATE-----\nclient cert for mutual TLS\n-----END CERTIFICATE-----",
"keyfile": "-----BEGIN PRIVATE KEY-----\nkey file for mutual TLS\n-----END PRIVATE KEY-----"
}
}
}
Given the complexity of the settings, it'd be a good idea to check the logs of the CA server after it's provisioned, to ensure that it has been properly initialized and started.
